Protecting the research & education sector against cyber attacks
A crucial part of operating a network providing connectivity to research and education is security. That is why many R&E networks have a Computer Emergency Response Team, CERT, to handle security incidents. And as cyber attacks increase steadily in frequency and scale, the importance of defending ones own network against attackers increases as well.
In this effort R&E network CERTs collaborate closely, both with each other and with CERTs operated by commercial network providers.
Most powerful DDoS attack
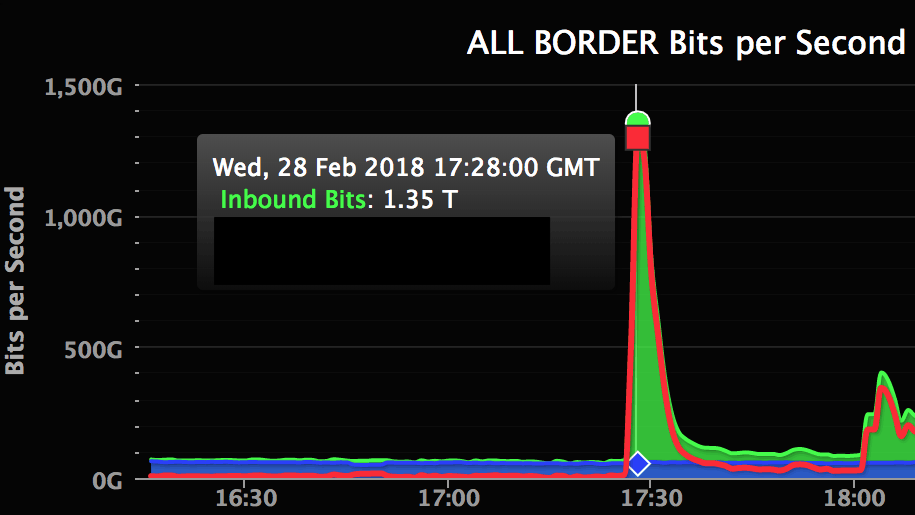
Wednesday 28. February 2018, cyber attackers launched the most powerful DDoS attack ever registered (image above). The target was Github, the world’s largest software development platform. A Distributed Denial of Service (DDoS) attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. In this specific attack up until 1,3 terabit data per second was directed against Github’s servers.
Security experts assume that China was behind the attack, attempting to block the access to anti censorship tools located on Github. One of these tools being a project page of the GreatFire.org service monitoring the censoring of online content conducted by Chinese authorities, commonly known as «The Great Firewall of China».
Traffic limit
In attacks like this the attackers try to utilize all the servers they can involve in the attack, regardless of them operating in commercial infrastructures or in r&e network infrastructures. But R&E network CERTs fight back. As an example the Nordic R&E network CERTs have set a traffic limit for a range of services often used for this kind of attacks. This means only a small amount of attack traffic can slip thorough. In this way the attacks can be controlled, although not prevented completely.
Unfortunately, attackers continuously try out new ways of evading the defence mechanisms set up by R&E network CERTs and other organizations fighting cyber attacks. In the Github attack mentioned above the attackers used servers handling the distributed memory caching system Memcached. The Nordic R&E network CERTs have now set up a traffic limit for this service also, to prevent future attacks.
For more information please contact our contributor(s):